PhD thesis defense to be held on February 14, 2024, at 17:00 (via Webex)
Picture Credit: Kostopoulos Nikos
Thesis title: Intelligent Services for Countering Domain Name System (DNS) Cyber Attacks in Software-Defined Network Infrastructures
Abstract: Domain Name System (DNS) maps symbolic identifiers (i.e. domain names) to various types of data, mainly IP addresses. Most network services depend on domain names for their operation, thus DNS is vital for the reliability of computer networks. This makes DNS a frequent target of Distributed Denial of Service (DDoS) attacks. One of the most devastating attack vectors against the DNS infrastructure is Water Torture, which floods Authoritative DNS Servers with invalid DNS requests to disrupt their name resolution services. Apart from DDoS attacks, DNS may also be employed to forward data pertaining to botnet activities. Domain Generation Algorithms (DGA's) abuse DNS to establish communications between compromised hosts (bots) and botnet orchestrators.
This dissertation addresses mechanisms for effectively protecting against threats targeting DNS infrastructures (i.e. Water Torture) or exploiting DNS messages for malicious purposes (i.e. DGA's). We overcome the limitations of traditional DNS security systems by employing Big Data methods (probabilistic data structures, Machine Learning - ML) and promising networking technologies (Software-Defined Networking, data plane programmability).
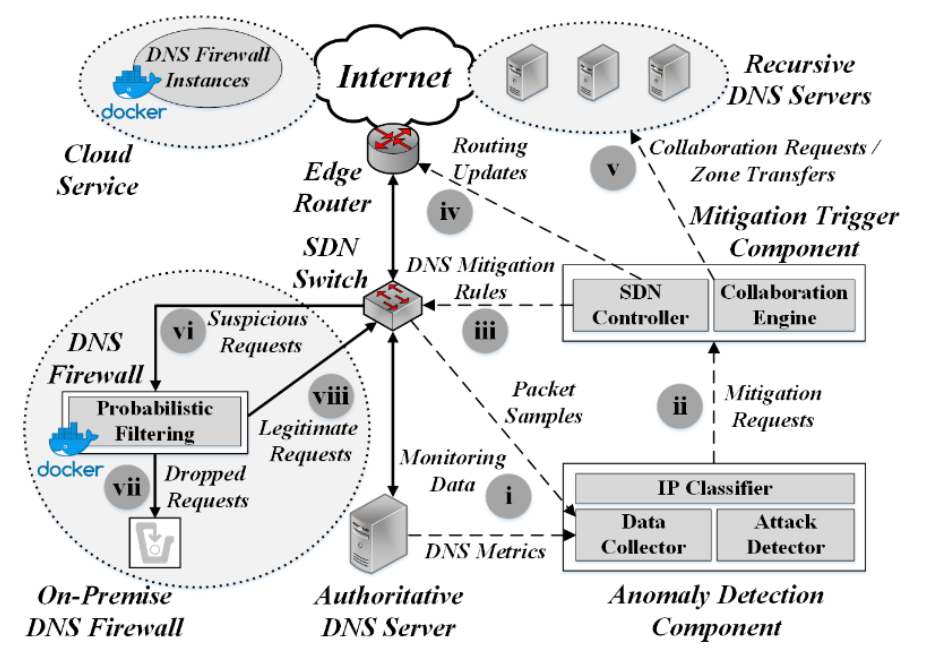
We initially propose a user-space schema that effectively detects and mitigates Water Torture attacks against Authoritative DNS Servers. Instead of processing plaintext names, we employ Bloom Filters (BF's) to map entire zone contents and filter DNS traffic in a time and space efficient manner. Our proposed mechanism categorizes requester IP addresses as legitimate or suspicious based on operations performed by probabilistic data structures (BF's, Count-Min Sketches) and deterministic spelling correction algorithms (SymSpell). DNS traffic from suspicious IP addresses is subsequently filtered based on BF contents. Malicious DNS requests are dropped, whereas benign requests are forwarded to the victim Authoritative DNS Server.
We subsequently employ data plane programmability to significantly improve the Water Torture attack filtering throughput of our user-space, BF-based mitigation mechanism. We rely on eXpress Data Path (XDP) to efficiently perform DNS Deep Packet Inspection (DPI) and rapidly discern benign and malicious requests at the Authoritative DNS server data plane. Contrary to other data plane programming approaches that require specialized hardware (e.g. P4 switches) or bypass the Linux kernel (e.g. Data Plane Development Kit - DPDK), our XDP-based approach runs on low-cost Network Interface Cards (NIC's) and does not bypass the kernel, thus Linux utilities (e.g. TCP/IP libraries) are available to developers.
We then propose a privacy-aware mechanism to facilitate Authoritative DNS Server zone distribution to external mitigation systems operating at Recursive DNS Servers (Recursors) or upstream scrubbing facilities. Without requiring formal agreements, our mechanism may enable administrators to filter DNS DDoS attacks more efficiently closer to their origins or DGA traffic with higher accuracy. Zones are mapped within Cuckoo Filters due to their time, space and dynamic element update advantages over BF's.
The aforementioned mechanisms depend on zone contents. However, Authoritative DNS Server administrators may be unwilling to collaborate due to security concerns. To that end, we complement our zone-based approaches for Water Torture attack mitigation by employing XDP to accelerate ML feature extraction and inference within the data plane of Recursors. Our approach relies on Naive Bayes Classifiers, which effectively segregate benign from DDoS attack DNS requests entirely within the Linux kernel. Thus, DNS attack mitigation throughput is significantly improved without requirements for any specialized hardware, e.g. Graphics Processing Units (GPU's).
Finally, we employ eXplainable Artificial Intelligence (XAI) techniques, specifically SHapley Additive exPlanation (SHAP), to interpret the decisions of binary ML classifiers that differentiate between legitimate names and malicious ones produced by DGA's. SHAP operates in a model-agnostic, post-hoc manner, i.e. regardless of the utilized ML algorithm and after the completion of the learning phase; this enables the analysis of tree and deep neural network classifiers in a unified fashion. Based on various SHAP visualization tools (summary, dependence, force plots), we derive global and local model interpretations on multiple and single dataset sample points respectively; these enable us to estimate feature importance and assess feature interactions. Our approach relies on features that capture name statistical and linguistic properties, thus time-consuming and privacy sensitive operations to obtain historical data are avoided. Our evaluation focuses on determining how name classification decisions are affected by specific DGA schemes (i.e. arithmetic, wordlist, hash and permutation-based) used for name construction.
Our proposed DNS protection mechanisms are evaluated via proof-of-concept setups within our laboratory virtualized infrastructure based on datasets widely employed by the research community and synthetic traffic generated based on our experience from the National Technical University of Athens (NTUA) campus network services.
Supervisor: Professor Emeritus Vasilis Maglaris
PhD Student: Kostopoulos Nikos
Connect via Webex:
https://centralntua.webex.com/centralntua/j.php?MTID=m10458a30537363e84cdb33f02eb85af0
